On & Off Site Data Protection
On-site Data Protection – Level 1
| Risks | Counter measure | Restore time |
|---|---|---|
| Virus attack | Snapshots | Instant |
| Data corruption | Self-healing | Instant |
| Disk failure | RAID | Instant |
| Rebuild failure | None | None |
| System failure | None | None |
| Natural disaster | None | None |
| Theft | None | None |
| Human error | None | None |
| Downtime | None | None |
- VFusionOS production server
On-site Data Protection - Level 2
| Risks | Counter measure | Restore time |
|---|---|---|
| Virus attack | Snapshots | Instant |
| Data corruption | Self-healing | Instant |
| Disk failure | RAID | Instant |
| Rebuild failure | Second RAID | Instant |
| System failure | None | None |
| Natural disaster | None | None |
| Theft | None | None |
| Human error | None | None |
| Downtime | None | None |
- VFusionOS production server
- Backup on local pool
On-site Data Protection - Level 3
| Risks | Counter measure | Restore time |
|---|---|---|
| Virus attack | Snapshots | Instant |
| Data corruption | Self-healing | Instant |
| Disk failure | RAID | Instant |
| Rebuild failure | Second RAID | Instant |
| System failure | Backup server | Instant |
| Natural disaster | None | None |
| Theft | None | None |
| Human error | None | None |
| Downtime | None | None |
- VFusionOS production server
- Backup on local pool
- Backup on system in same location
On- & Off-site Data Protection
| Risks | Counter measure | Restore time |
|---|---|---|
| Virus attack | Snapshots | Instant |
| Data corruption | Self-healing | Instant |
| Disk failure | RAID | Instant |
| Rebuild failure | Second RAID | Instant |
| System failure | Backup server | Instant |
| Natural disaster | Remote server | Hours |
| Theft | Remote server | Hours |
| Human error | Remote server | Hours |
| Downtime | None | None |
- VFusionOS production server
- Backup on local pool
- Backup on system in same location
- Backup on remote site
On- & Off-site Data Protection with HA Cluster
| Risks | Counter measure | Restore time |
|---|---|---|
| Virus attack | Snapshots | Instant |
| Data corruption | Self-healing | Instant |
| Disk failure | RAID | Instant |
| Rebuild failure | Second RAID | Instant |
| System failure | Backup server | Instant |
| Natural disaster | Remote server | Hours |
| Theft | Remote server | Hours |
| Human error | Remote server | Hours |
| Downtime | High Availability | Instant |
- VFusionOS production server
- Backup on local pool
- Backup on system in same location
- Backup on remote site
- Set up another VFusionOS backup server in another building, city or even country!Set up another VFusionOS backup server in another building, city or even country!
- Send your backups to the most remote location using a public network – for enhanced protection of your data, and ensuring it’s secure even when all local servers are completely unavailable, for example as a result of fire or theft.
- ou can have multiple off-site backup servers in multiple locations at the same time.
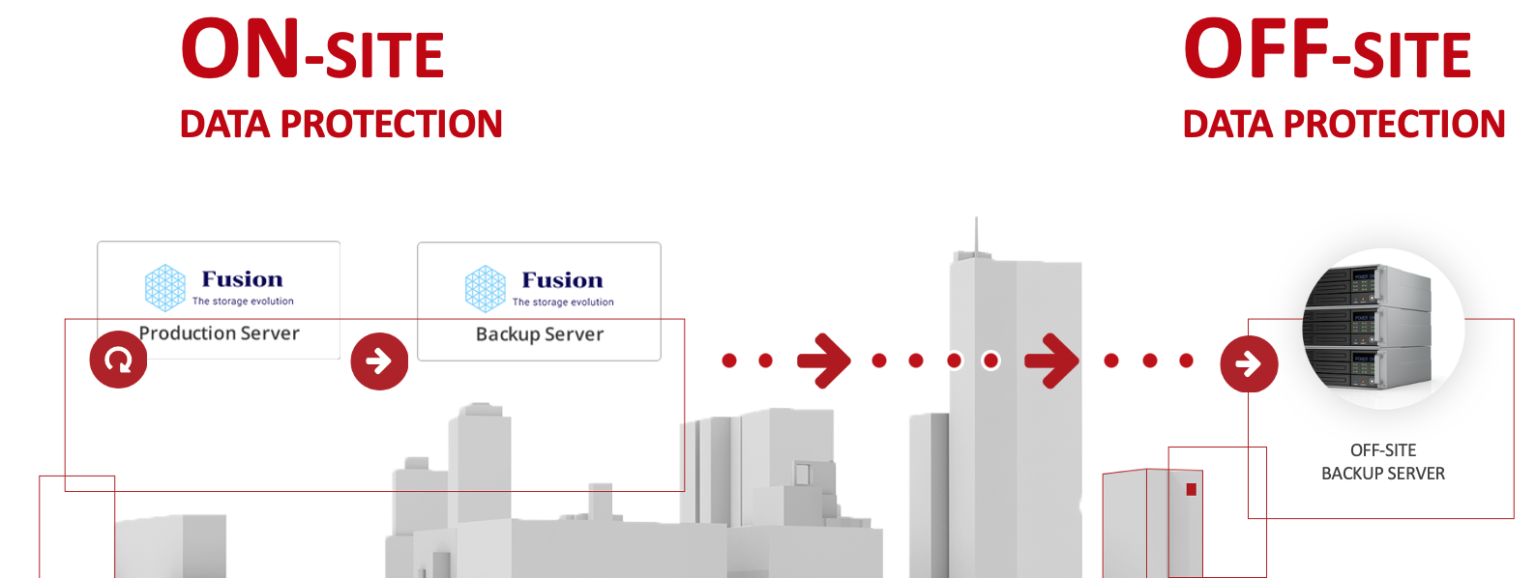
The Infrastructure
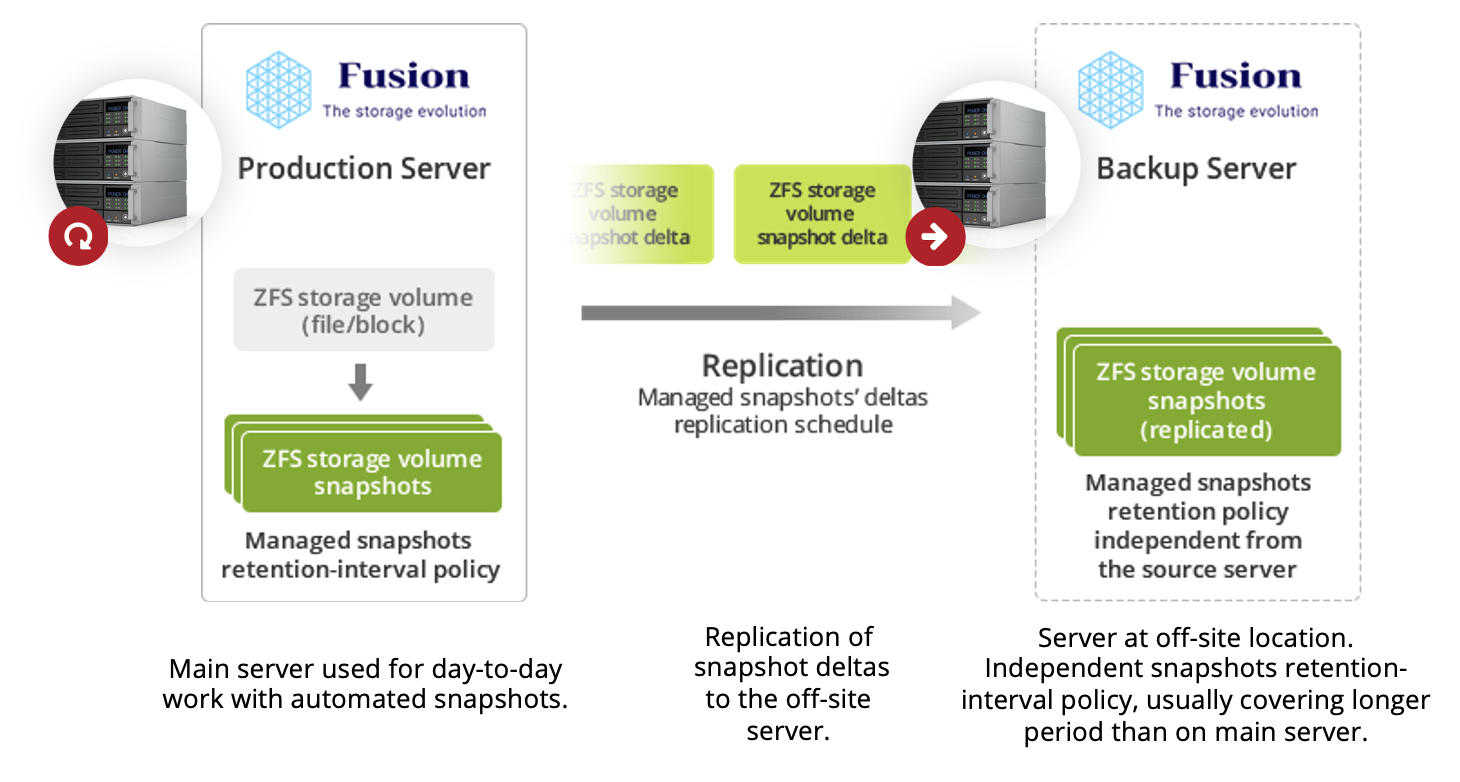
Backup timeline
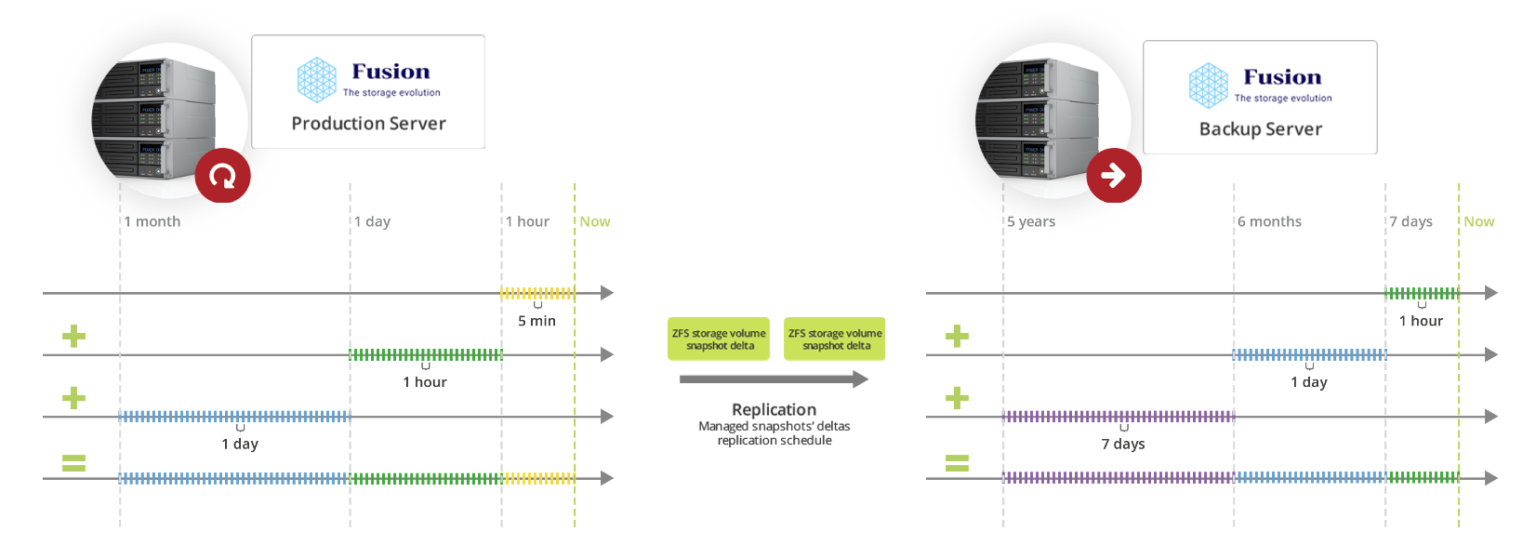
On both local and off-site locations there are independent snapshots retention policies for
- Making new snapshots as often as 5 minutes.
- Keeping snapshots even for years without running out of space.
Disaster Recovery Plan
Everyone knows that having a backup solution is a must but backup policies always differ depending on significance, type etc. of company data. For instance, important data used by the whole company on a daily basis and where the loss of these data may even result in bankruptcy, should be secured at the highest level of protection. On the other hand, less important archived data that are kept for future purposes can be protected by a lower protection level e.g. one off-site backup copy only.
Most often, to fulfil data security needs of advanced environments, an additional Disaster Recovery plan is required. Such a plan is a combination of backup and other additional protection mechanisms e.g. disk redundancy or even server redundancy. All of those elements usually have to be provided by different third party tools, adding to overall costs and complexity.
VFusionOS with On- & Off-site Data Protection doesn’t require any additional tools and supports many types of backup schemes which is why this software with High Availability and other built-in protection mechanisms is a perfect solution for even the most advanced Disaster Recovery plans.

VFusionOS with On- & Off-site Data Protection doesn’t require any additional tools and supports many types of backup schemes which is why this software with High Availability and other built-in protection mechanisms is a perfect solution for even the most advanced Disaster Recovery plans.
What are the key factors to measure the efficiency of disaster recovery?
RPO – Recovery Point Objective
Amount of time between the incident that caused data loss or corruption and the time of the last successful backup.
Smaller RPO = better.
RTO – Recovery Time Objective
Amount of time required to restore the data and successfully resume the company’s operations.
Smaller RTO = better.


Data Protection both RPO and RTO
With Off-site Data Protection both RPO and RTO can be counted in minutes. These parameters are among the best in the industry!
Data Protection Levels
Off-site VS High Availability Cluster
Off-site Data Protection complements High Availability Clusters but does not replace them!
Off-Site Data Protection
- Protects data by constantly backing it up and storing copies both locally and remotely.
- Allows restoring data to a previous saved point in case of hardware failure or data corruption.


High Availability Cluster
- Ensures business continuity by providing uninterrupted access to data even during hardware failures.
- Maximizes utilization of hardware and network resources.
Off-site Data Protection is a solution that prevents and neutralizes threats on data security.
- Easy to use backup of mission-critical data with very light backup engine.
- Ability to backup full OSes (as virtual machines).
- Solved problem of Backup Window.
- Ability to store multiple copies of backups, including remote servers.
- Protection against ransomware.
- Immediate access and restore of previous data versions with recovery time as small as 5 minutes.
- Unparalleled flexibility of disaster recovery restore from 5 minutes or 2 years in the past if needed.
- Optional removal and rotation of backup media.
- Encrypted transport.

Seamless integration with High Availability Cluster for even greater data protection.

